


Threat actors have hijacked more than 35,000 registered domains in so-called Sitting Ducks attacks that allow claiming a domain without having access to the owner’s account at the DNS provider or registrar.
In a Sitting Ducks attack, cybercriminals exploit configuration shortcomings at the registrar level and insufficient ownership verification at DNS providers.
Researchers at DNS-focused security vendor Infoblox and at firmware and hardware protection company Eclypsium discovered that there are more than a million domains that can be hijacked every day via the Sitting Ducks attacks.
Threat actors have hijacked more than 35,000 registered domains in so-called Sitting Ducks attacks that allow claiming a domain without having access to the owner’s account at the DNS provider or registrar.
In a Sitting Ducks attack, cybercriminals exploit configuration shortcomings at the registrar level and insufficient ownership verification at DNS providers.
Researchers at DNS-focused security vendor Infoblox and at firmware and hardware protection company Eclypsium discovered that there are more than a million domains that can be hijacked every day via the Sitting Ducks attacks.
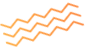
– the authoritative name server of the record cannot resolve queries because it lacks the info about the domain (lame delegation)
– the DNS provider needs to allow claiming a domain without properly verifying ownership or requiring access to the owner’s account
Variations of the attack include partially lame delegation (not all name servers are configured incorrectly) and redelegation to another DNS provider. However, if lame delegation and exploitable provider conditions are met, the domain can be hijacked.
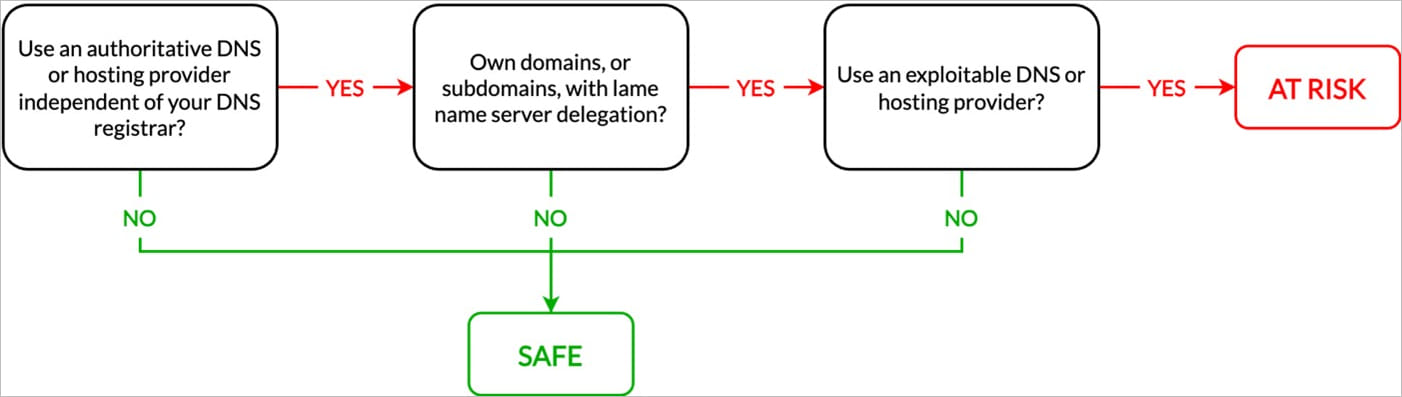
Infoblox explains that attackers can use the Sitting Ducks method on domains that use authoritative DNS services from a provider that is different from the registrar, such as a web hosting service.
If the authoritative DNS or web hosting service for the target domain expires, an attacker can simply claim it after creating an account with the DNS service provider.
The threat actor can now set up a malicious website under the domain and configure DNS settings to resolve IP address record requests to the fake address; and the legitimate owner won’t be able to modify the DNS records.
Infoblox and Eclypsium report that they have observed multiple threat actors exploiting the Sitting Ducks (or Ducks Now Sitting – DNS) attack vector since 2018 and 2019.
Since then, there have been at least 35,000 domain hijacking cases using this method. Typically, the cybercriminals held the domains for a short period but there were some instances where they kept them up to a year.